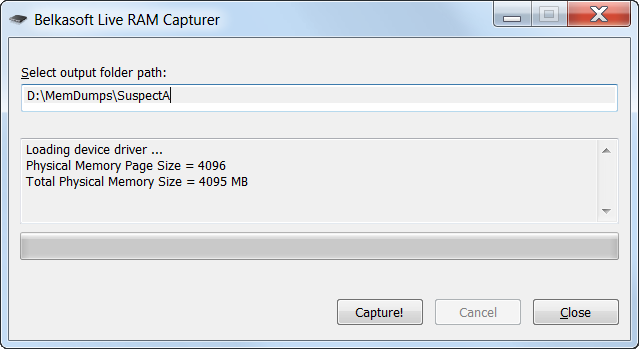
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 14 (Live Memory Forensics) « Null Byte :: WonderHowTo
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 14 (Live Memory Forensics) « Null Byte :: WonderHowTo

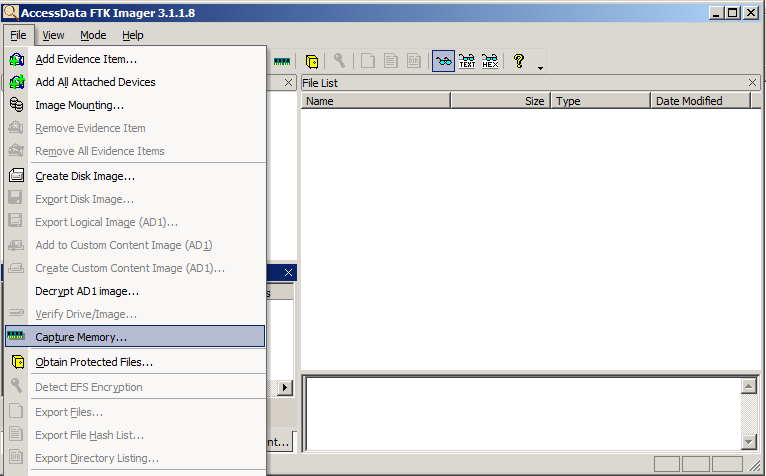
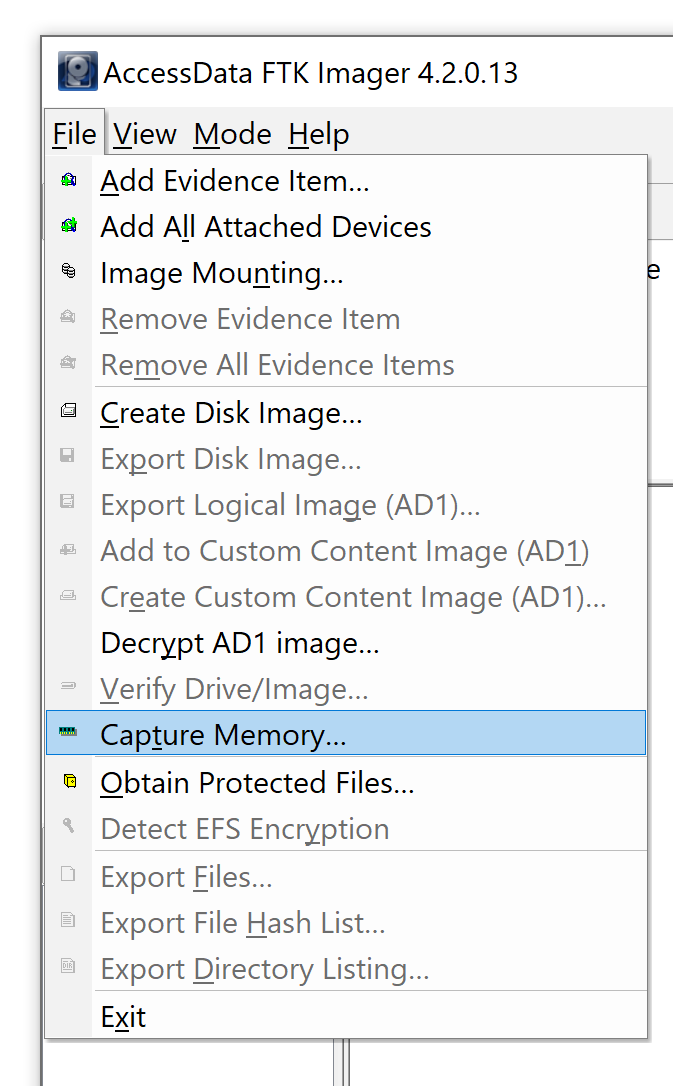
Forensic Report Sample:Volatile Memory Acquisition using FTK Imager Lite | by Vishal Thakur | Medium
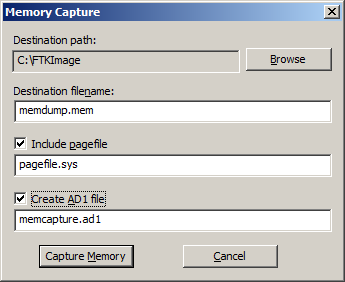
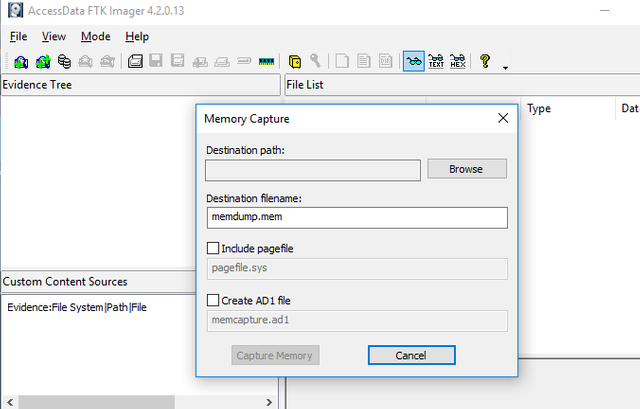
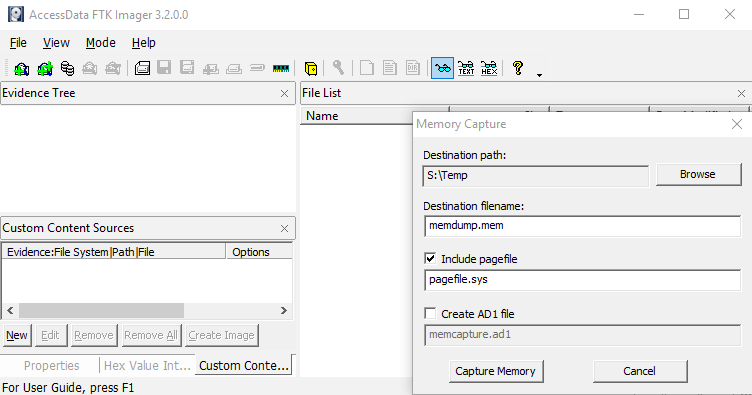
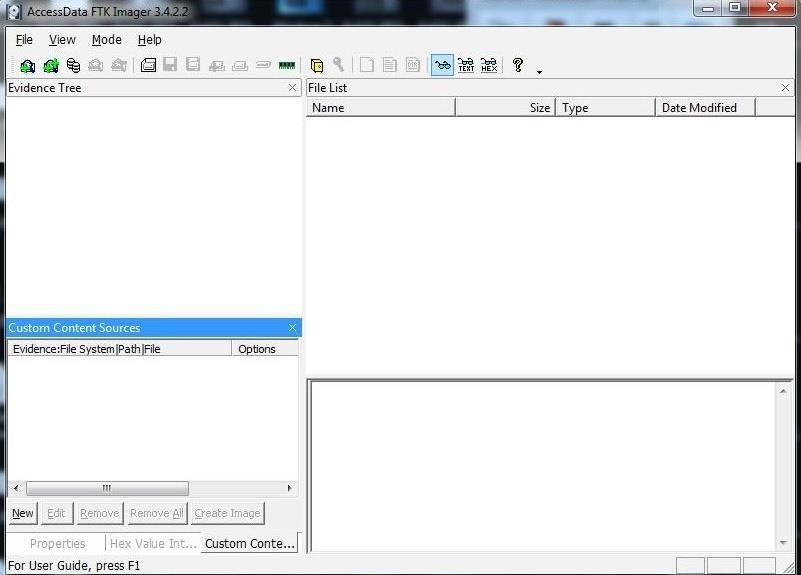
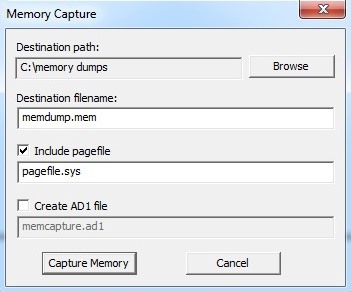
Capturing Memory and Obtaining Protected Files with FTK Imager – eDiscovery Best Practices - CloudNine

Forensic Report Sample:Volatile Memory Acquisition using FTK Imager Lite | by Vishal Thakur | Medium

Capturing Memory and Obtaining Protected Files with FTK Imager – eDiscovery Best Practices - CloudNine