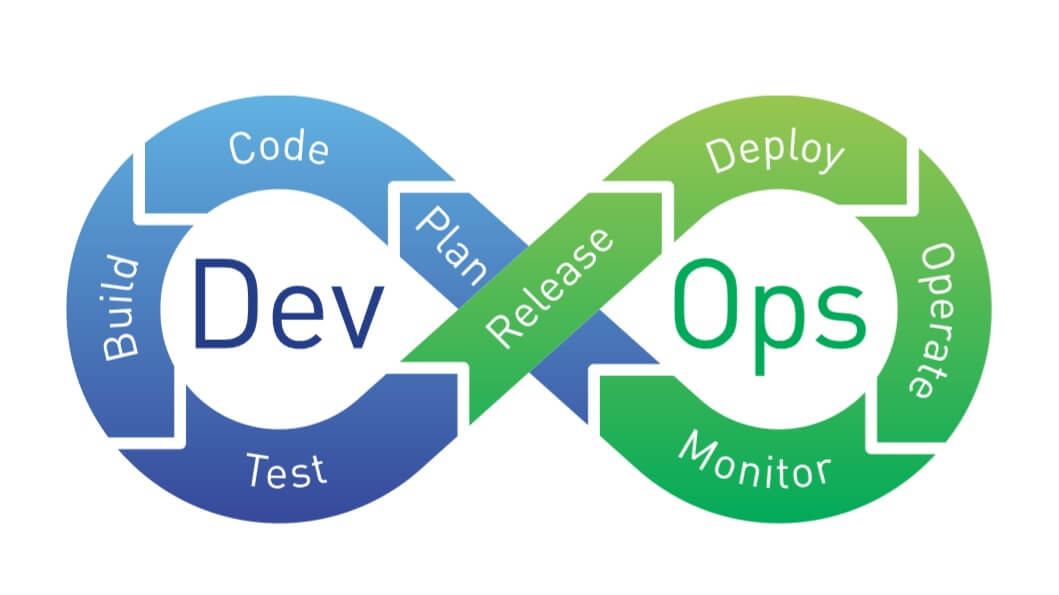
The different stages of a CI/CD pipeline with the emphasis on parallel... | Download Scientific Diagram

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

Cloud & Network automation challenge: Deploy Security Rules in a DevOps/GitOps world with AWS, Terraform, GitLab CI, Slack, and Python (special guest FastAPI) - part 1/3 • Adrian Giacometti

How do we secure ManoMano applications with our DIY pipeline ? | by Laurent Delosieres | ManoMano Tech team | Medium





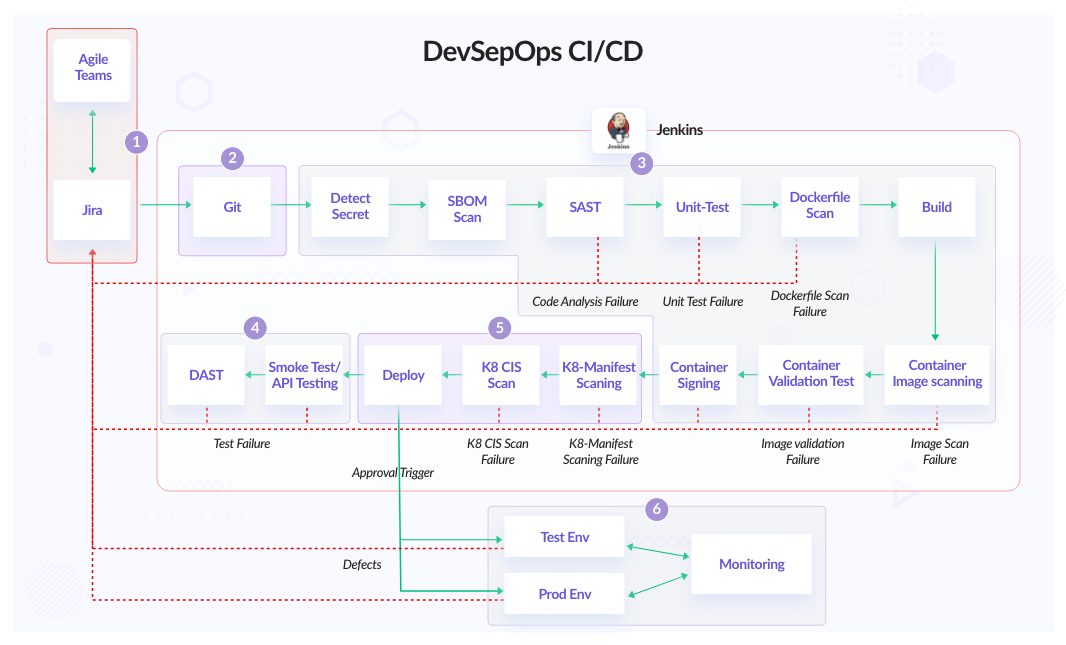

![Checking Terraform IaC security in CI/CD with Regula and Bitbucket Pipelines [Tutorial] Checking Terraform IaC security in CI/CD with Regula and Bitbucket Pipelines [Tutorial]](https://www.fugue.co/hubfs/Screen%20Shot%202021-12-28%20at%203.43.01%20PM.png)




![Compromising CI/CD Pipelines with Leaked Credentials [Security Zines] Compromising CI/CD Pipelines with Leaked Credentials [Security Zines]](https://blog.gitguardian.com/content/images/2022/04/22W15-blog-SecurityZines-Compromising_CICD_pipelinesnal.jpg)