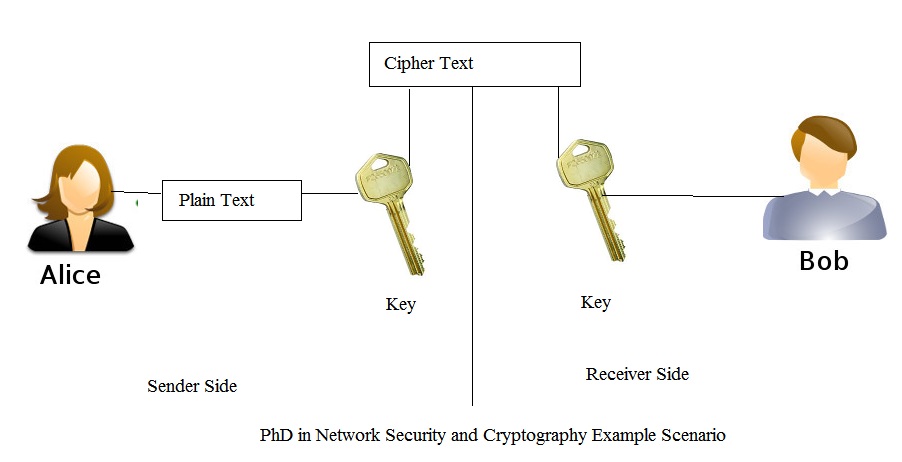
An analytic study of architecture, security, privacy, query processing, and performance evaluation of database‐as‐a‐service - Khan - 2022 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Futuristic view of the Internet of Quantum Drones: Review, challenges and research agenda - ScienceDirect

An efficient outsourced attribute-based encryption scheme in the device-to-device mobile network - Huawei Wang, Ye Li, Yingnan Jiao, Zhengping Jin, 2019
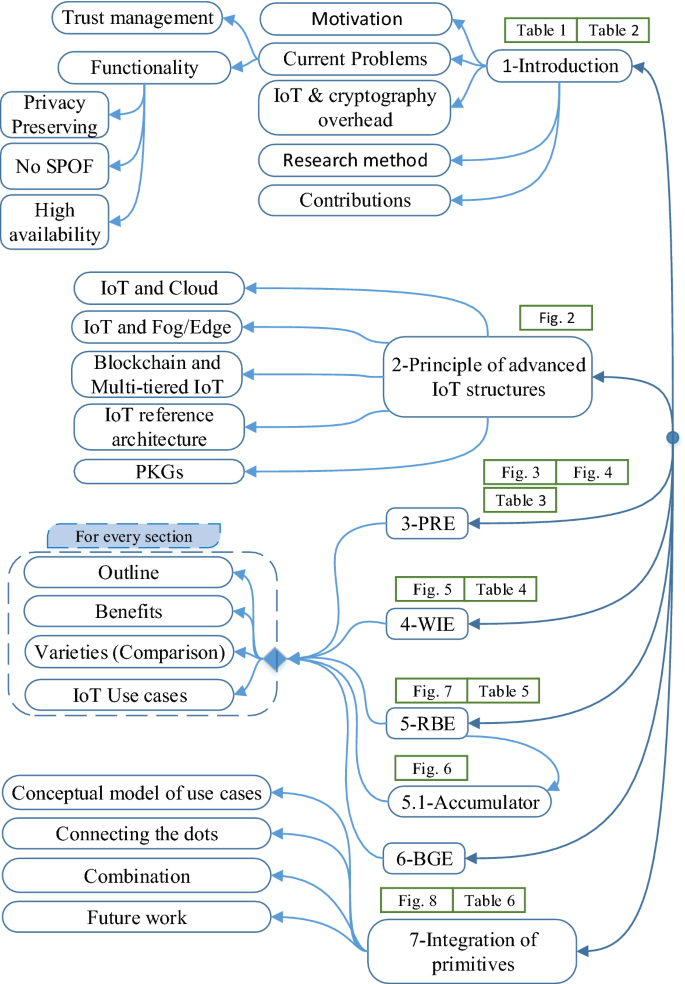
Advanced encryption schemes in multi-tier heterogeneous internet of things: taxonomy, capabilities, and objectives | SpringerLink
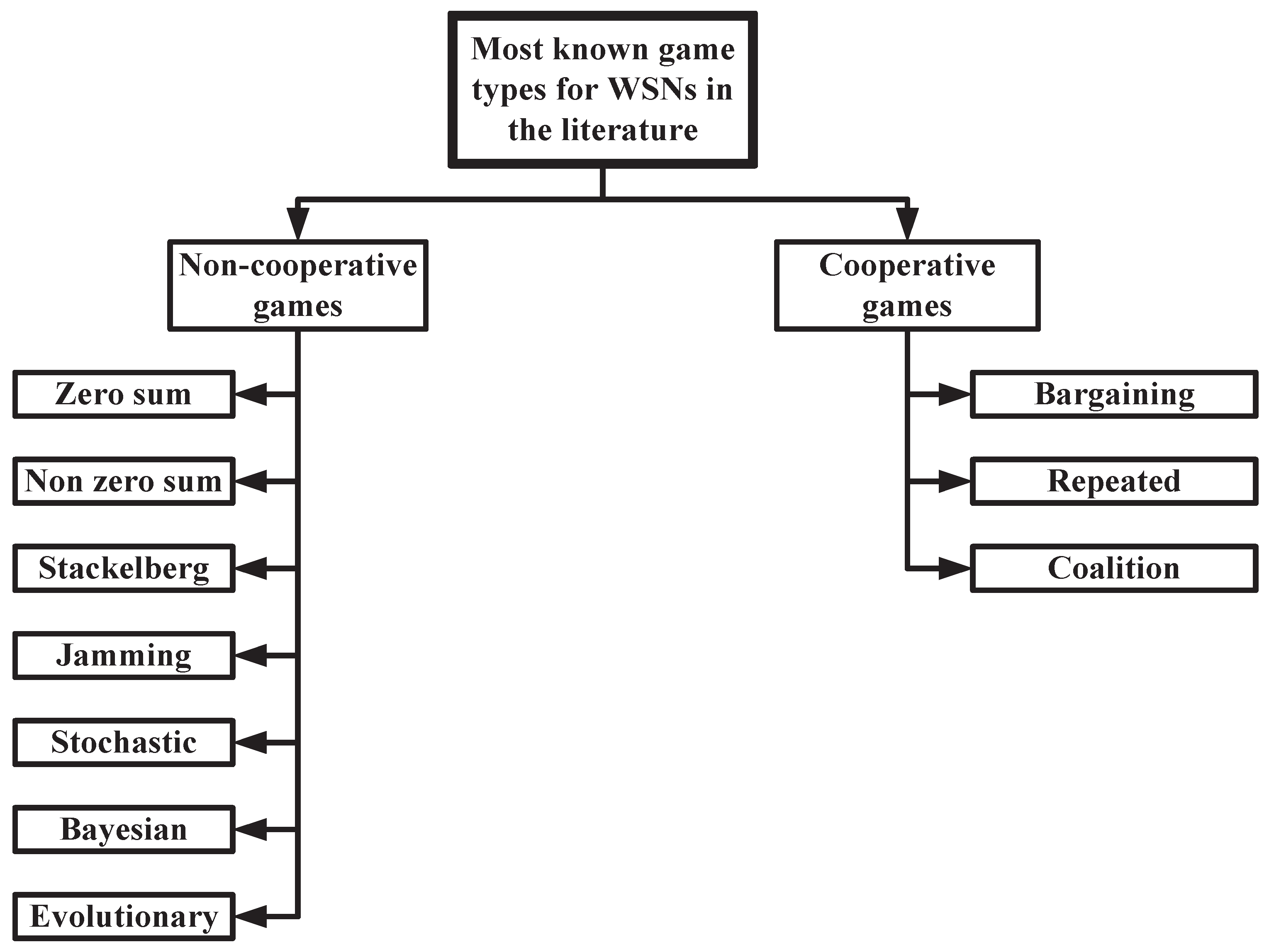
Sensors | Free Full-Text | Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey

PDF) TOP 10 CITED PAPERS FOR CRYPTOGRAPHY AND INFORMATION SECURITY | International Journal on Cryptography and Information Security (IJCIS) - Academia.edu

IoT | Free Full-Text | AI-Inspired Non-Terrestrial Networks for IIoT: Review on Enabling Technologies and Applications
![PDF) [PhD Thesis] On the use of homomorphic encryption to secure cloud computing, services, and routing protocols | Youssef Gahi - Academia.edu PDF) [PhD Thesis] On the use of homomorphic encryption to secure cloud computing, services, and routing protocols | Youssef Gahi - Academia.edu](https://0.academia-photos.com/attachment_thumbnails/38613758/mini_magick20180818-12937-1tgaygw.png?1534650796)