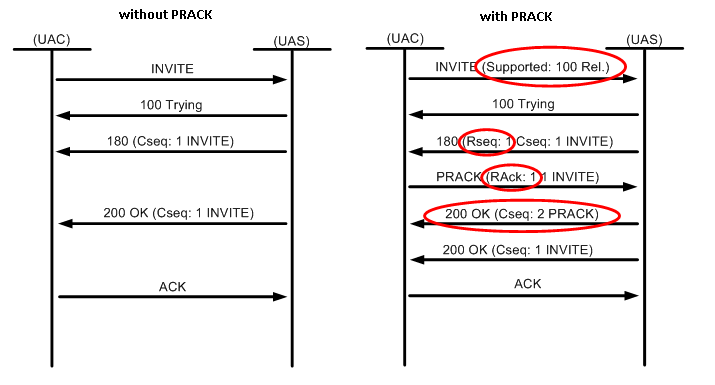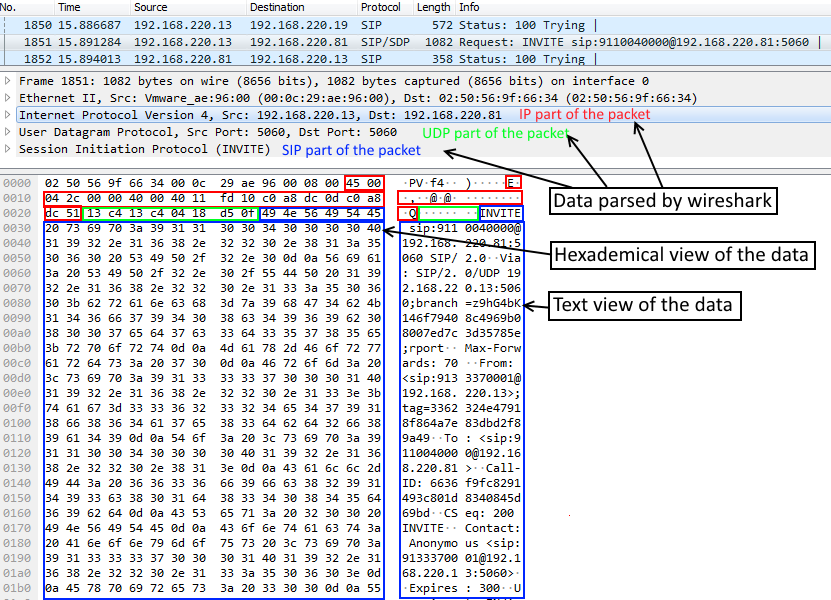
PDF) Encrypted Network Traffic Analysis of Secure Instant Messaging Application: A Case Study of Signal Messenger App

A framework for digital forensics of encrypted real-time network traffic, instant messaging, and VoIP application case study - ScienceDirect

Applied Sciences | Free Full-Text | Encrypted Network Traffic Analysis of Secure Instant Messaging Application: A Case Study of Signal Messenger App

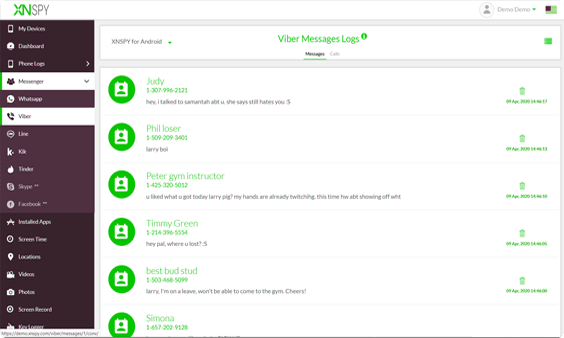
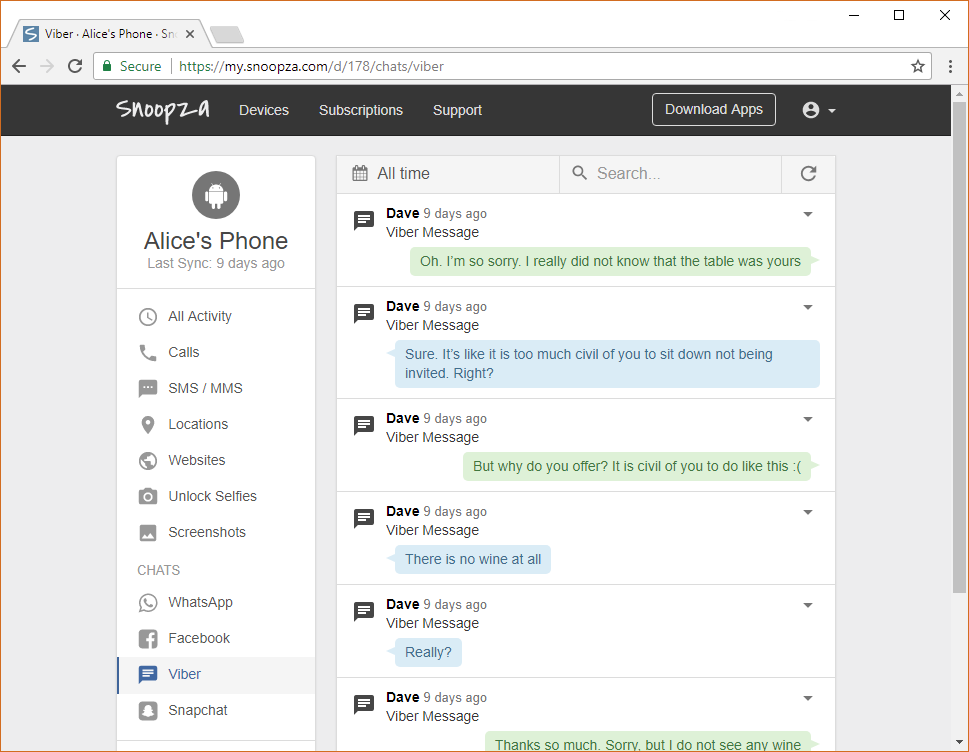
Can my employer read my Viber messages (I used Viber on a desktop) since I was on the employer's network? I know the messages are encrypted but how would that help if

A framework for digital forensics of encrypted real-time network traffic, instant messaging, and VoIP application case study - ScienceDirect