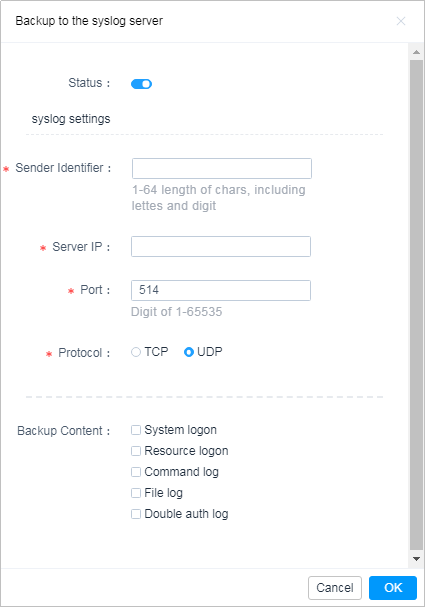
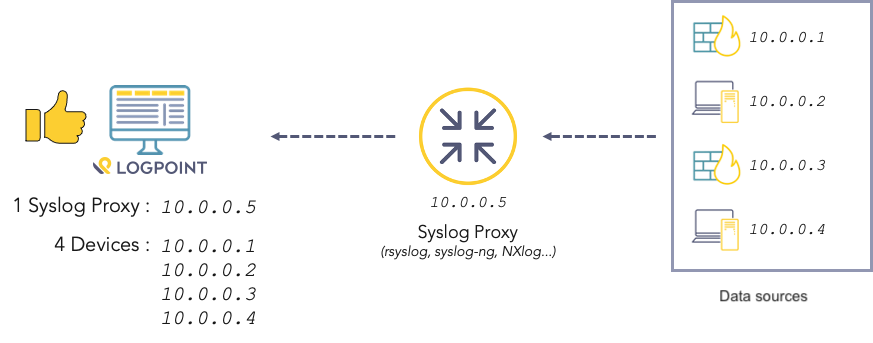
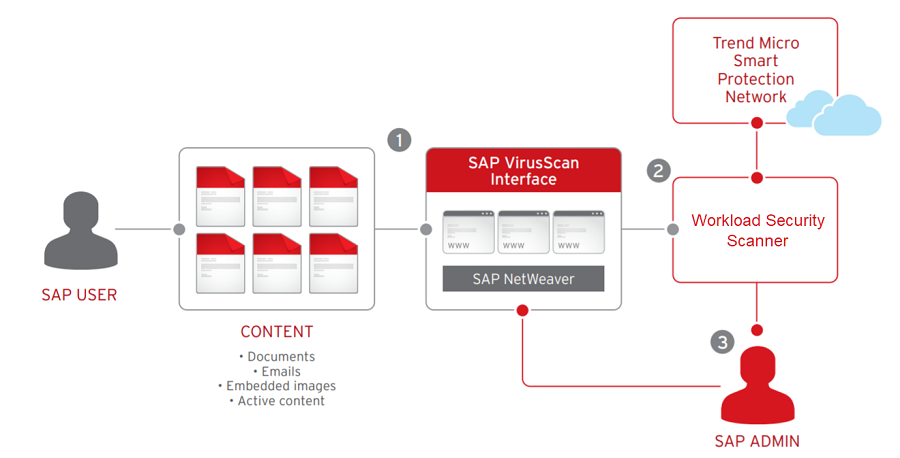
SAP Security Audit Logs: Which event types should I enable? There are 90 of them! And how much disk space do I need? | SAP Blogs

SUSE Linux Enterprise Server for SAP Applications 12 | Operating System Security Hardening Guide for SAP HANA for SUSE Linux Enterprise Server 12