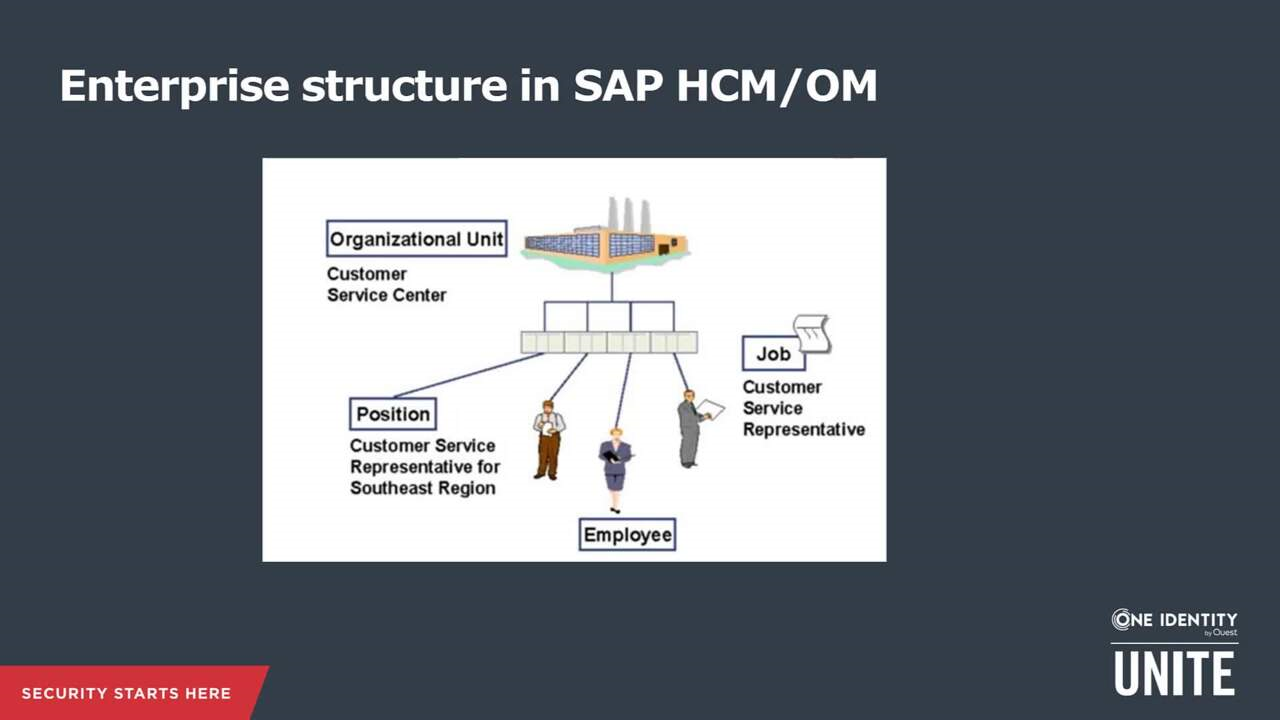
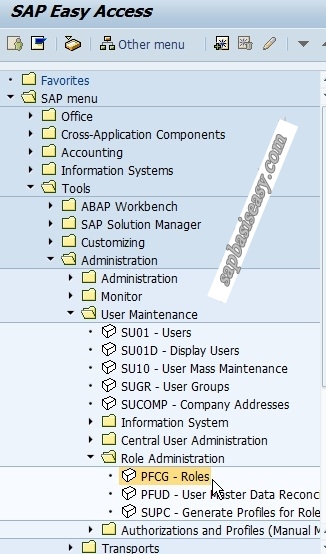
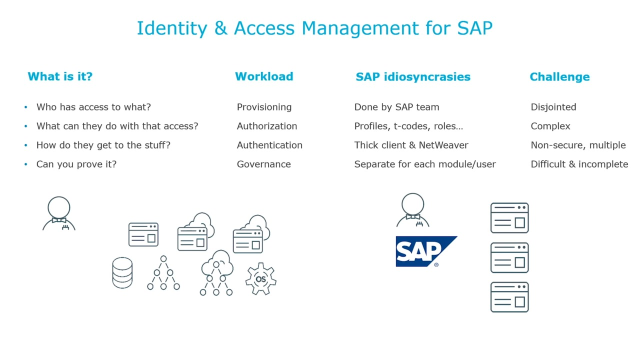
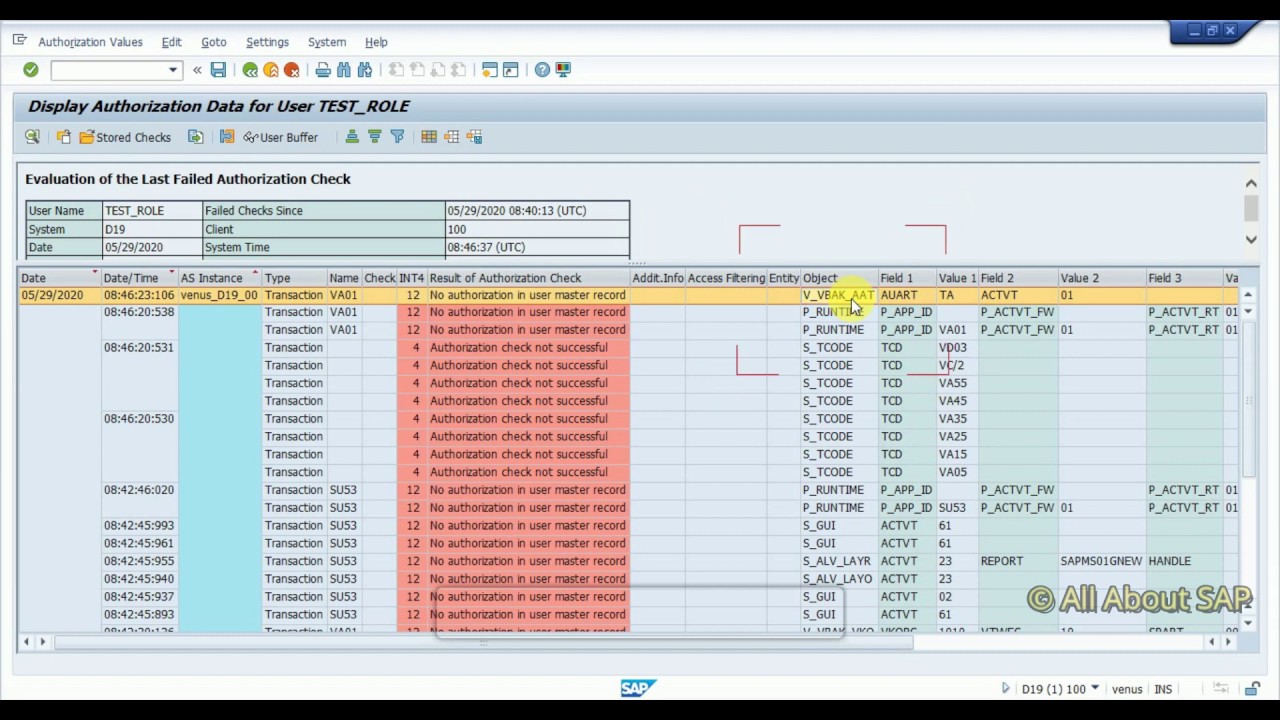
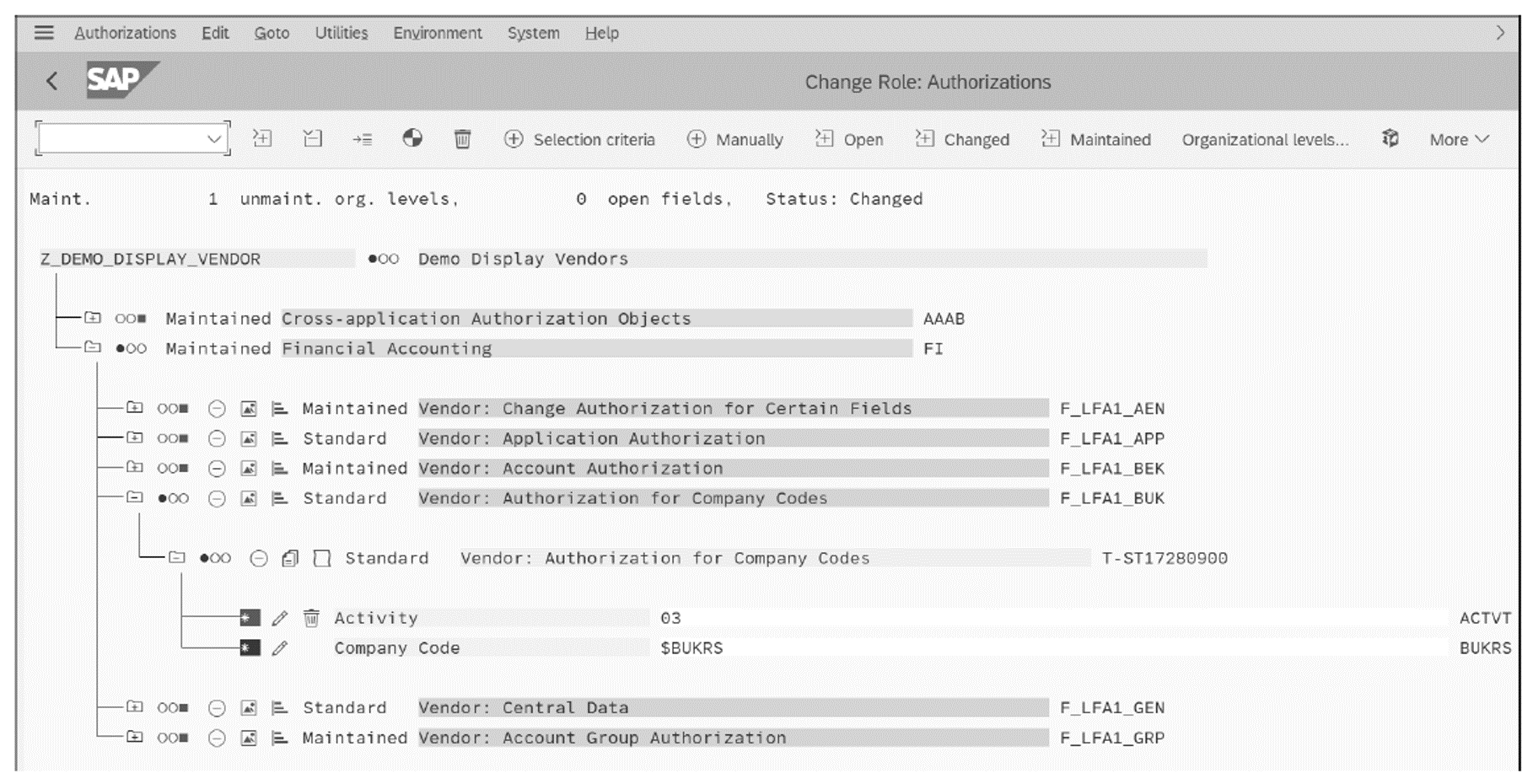
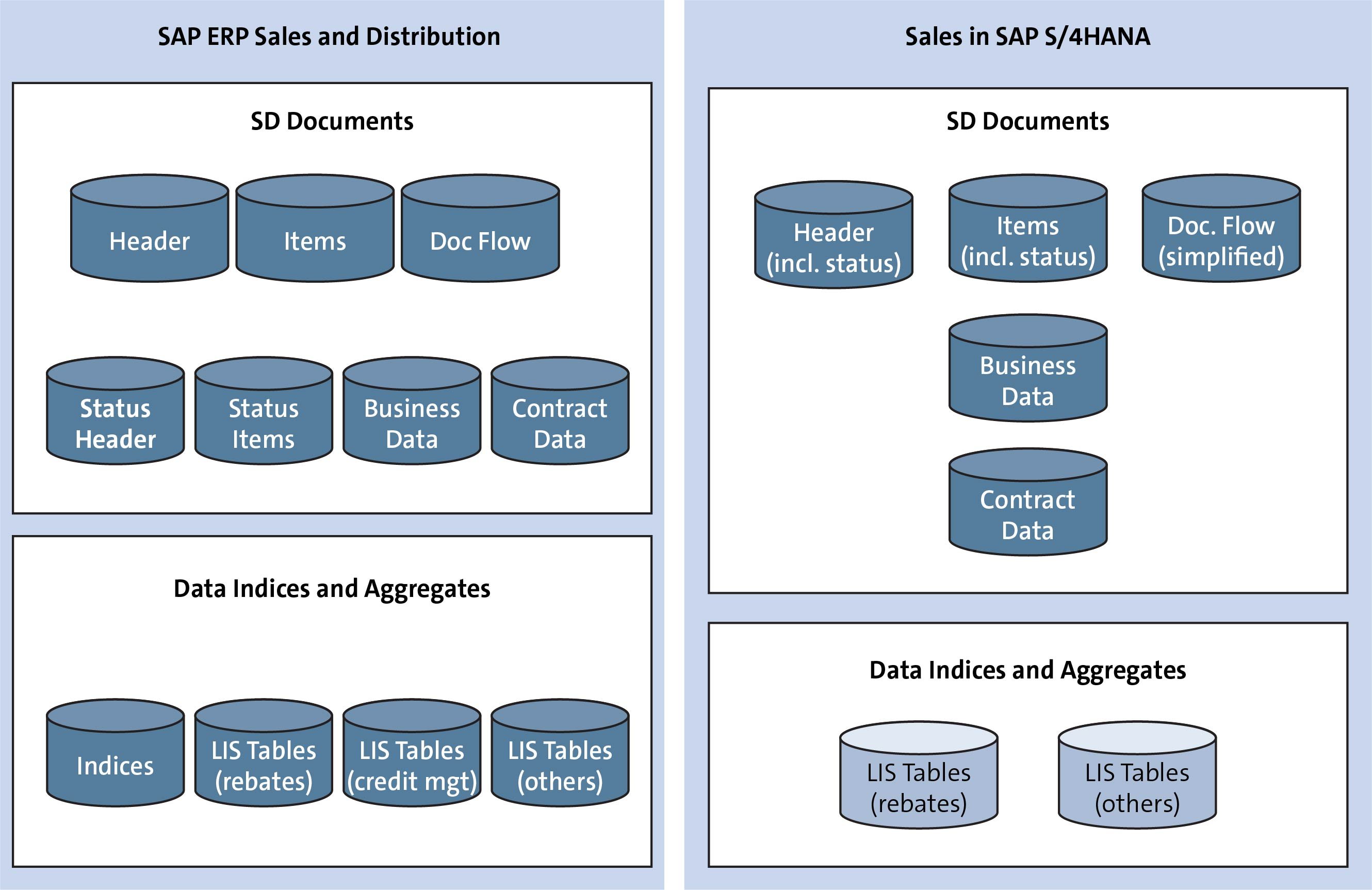
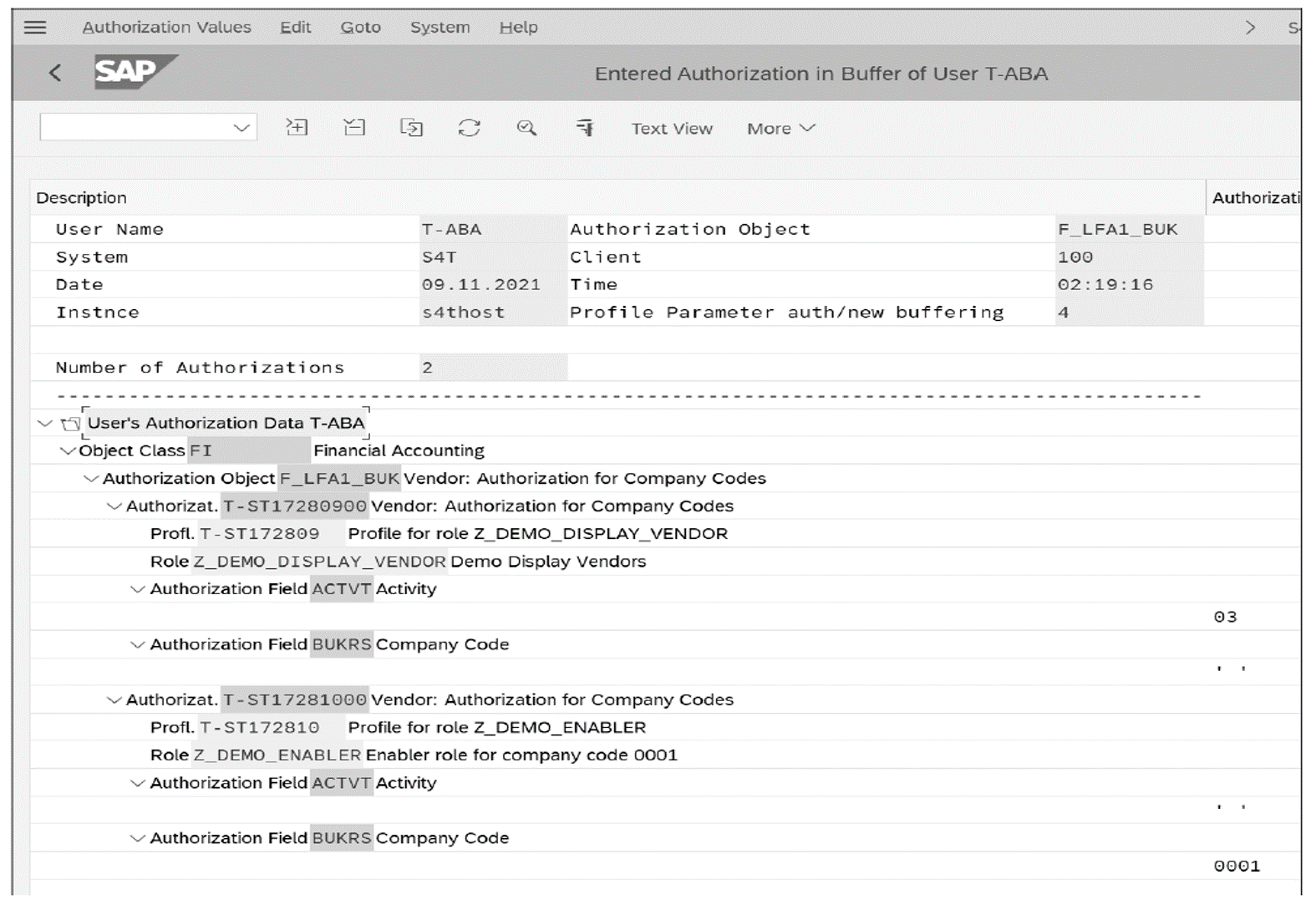
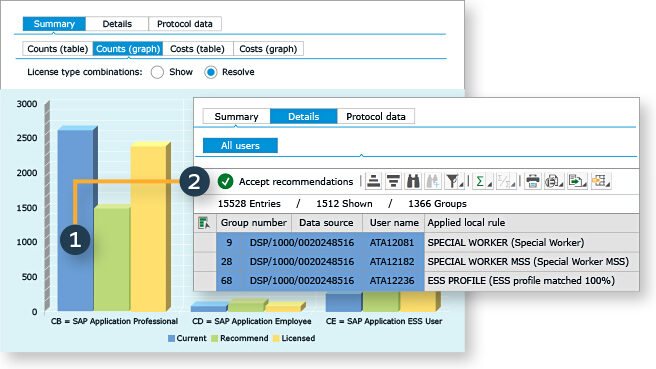
Identity Management and SAP Users, Roles and Transactions - Part1 - IBM Security Identity and Access

How to aggregate and visualize AWS Health events using AWS Organizations and Amazon Elasticsearch Service | AWS Cloud Operations & Migrations Blog

Identity Management and SAP Users, Roles and Transactions - Part1 - IBM Security Identity and Access

Using delegated admin for AWS Config operations and aggregation | AWS Cloud Operations & Migrations Blog