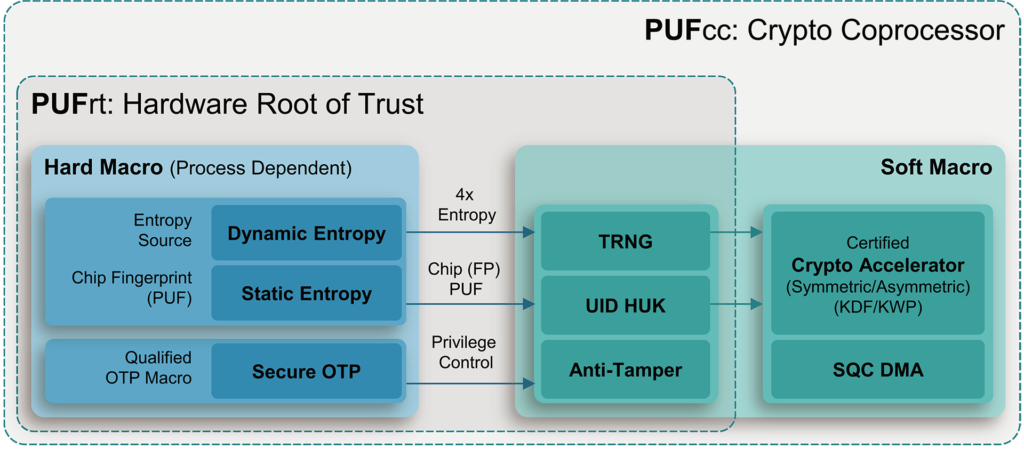
Microchip Adds Real-Time Security to Its Root of Trust Silicon Tech | Data Center Knowledge | News and analysis for the data center industry
Privilege escalation with polkit: How to get root on Linux with a seven-year-old bug | The GitHub Blog
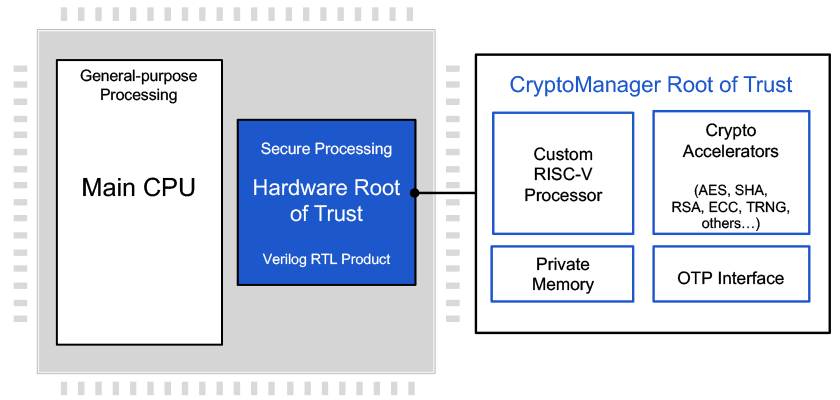
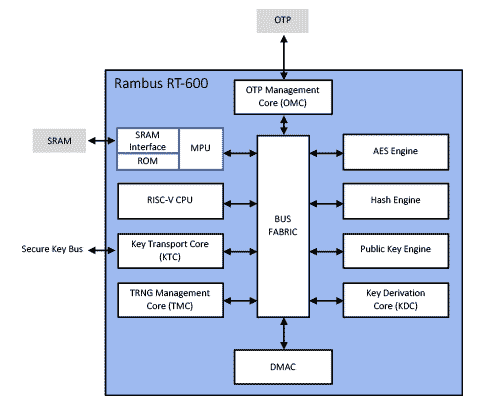
Rambus CryptoManager Root of Trust Cores Certified ASIL-B/D Ready for Enhanced Security in Automotive Applications - Rambus