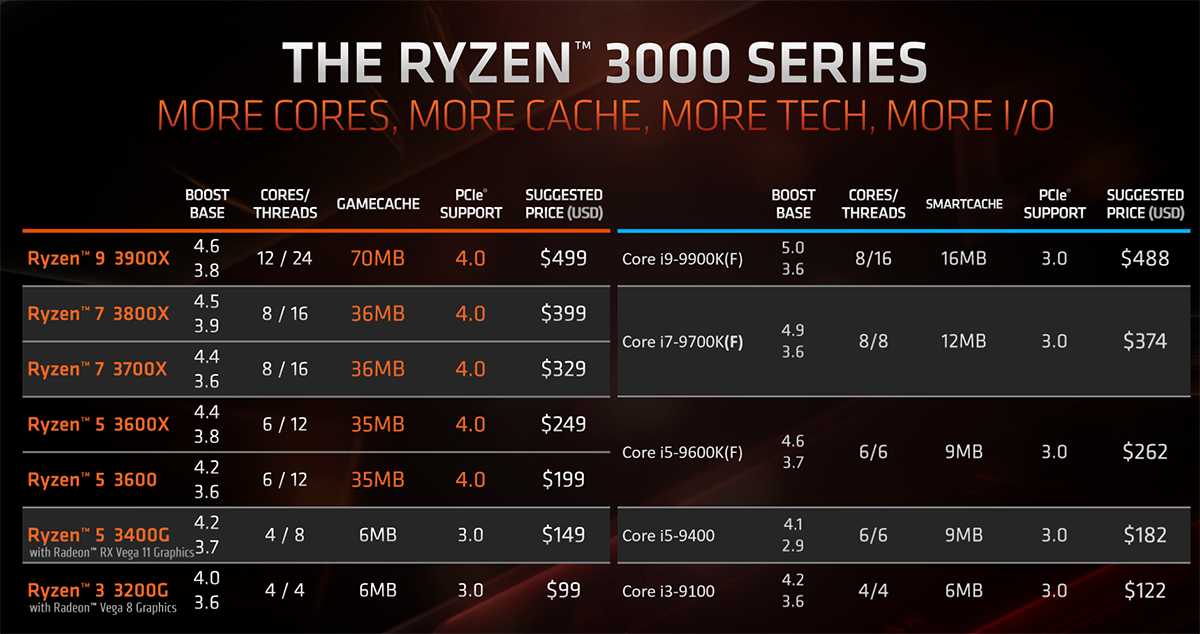
Amd Ryzen 5 5600g R5 5600g 3.9ghz Six-core Twelve-thread 65w Cpu Processor L3=16m 100-000000252 Socket Am4 No Fan - Cpus - AliExpress
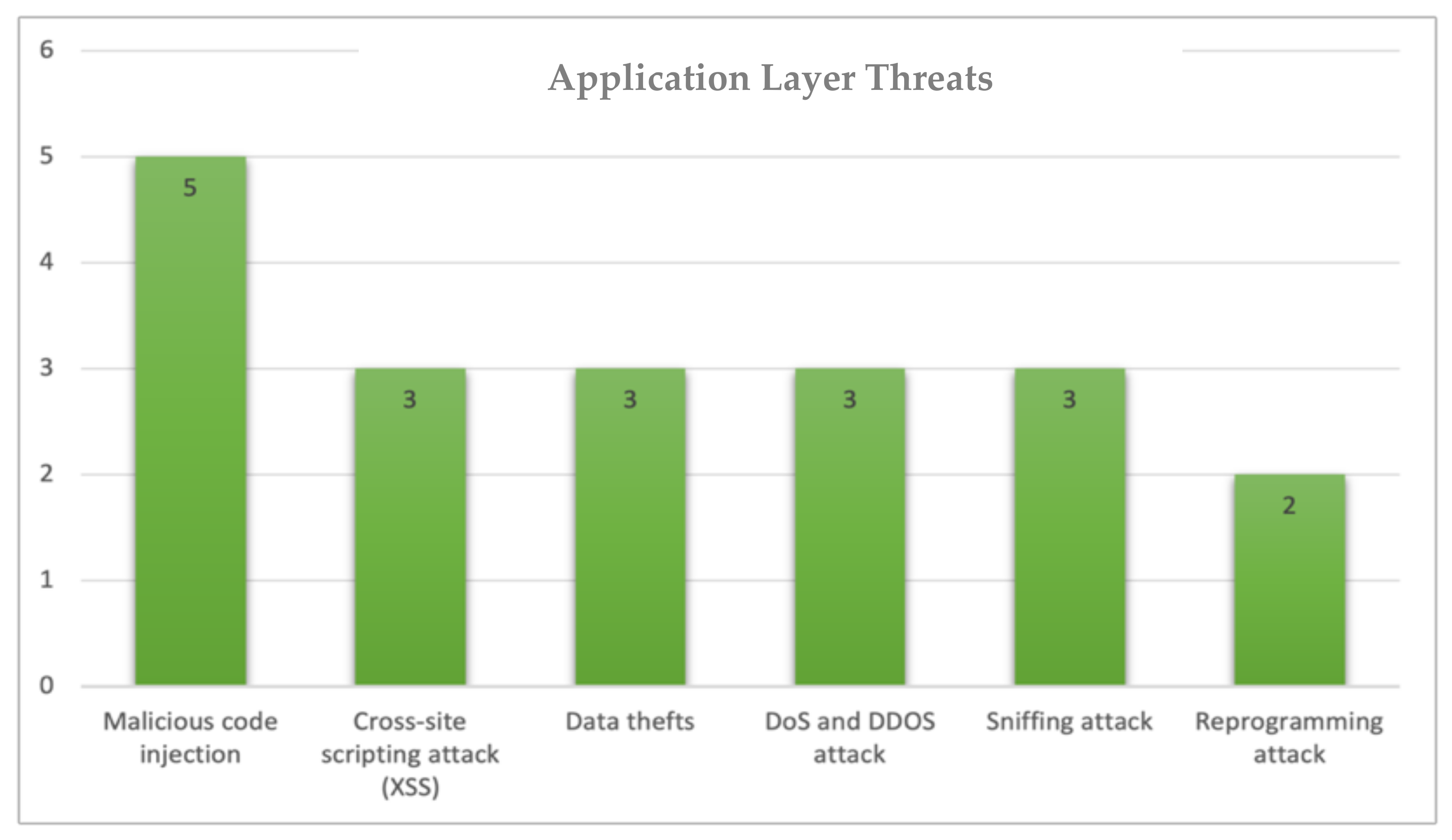
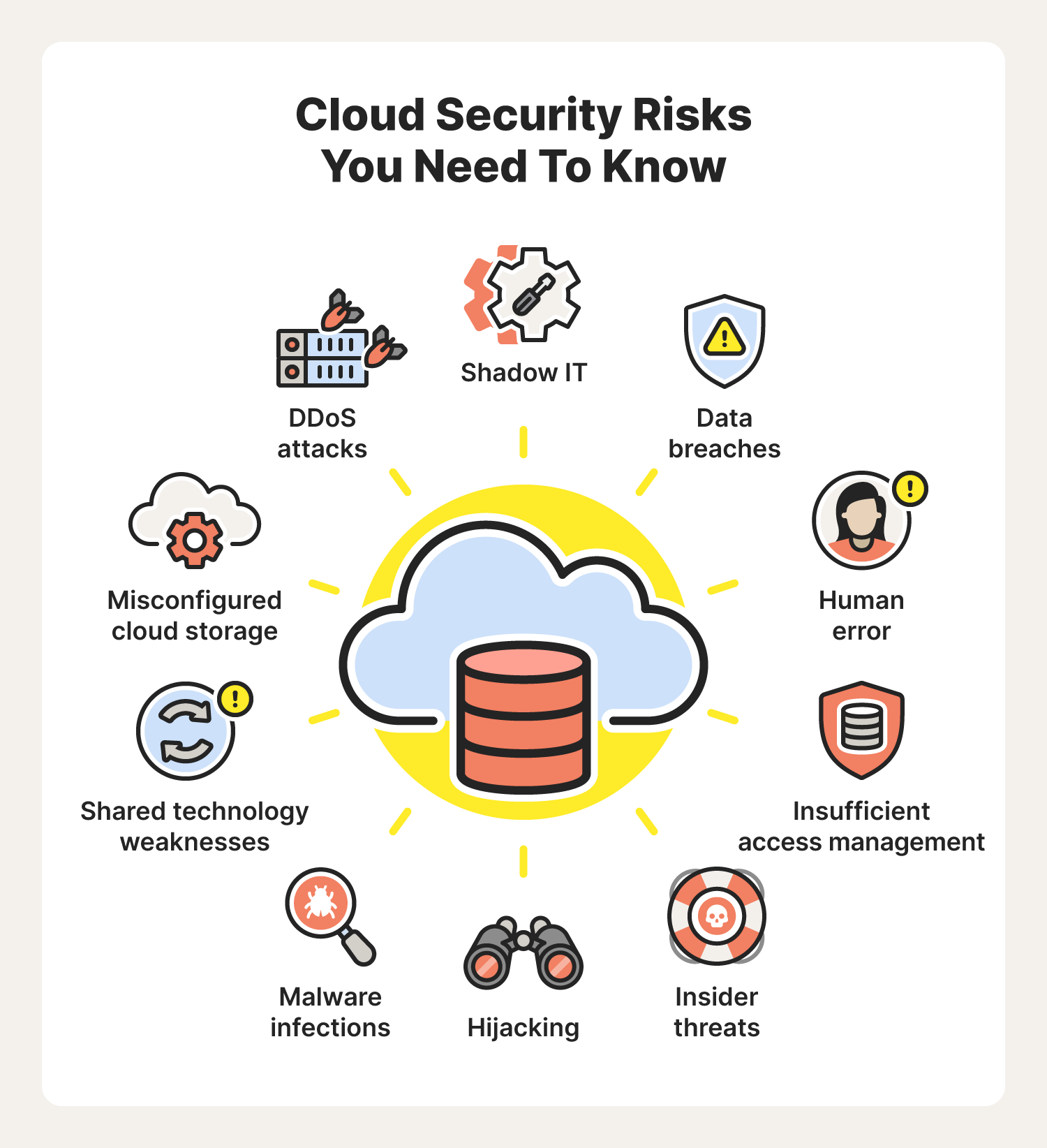
Electronics | Free Full-Text | Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions
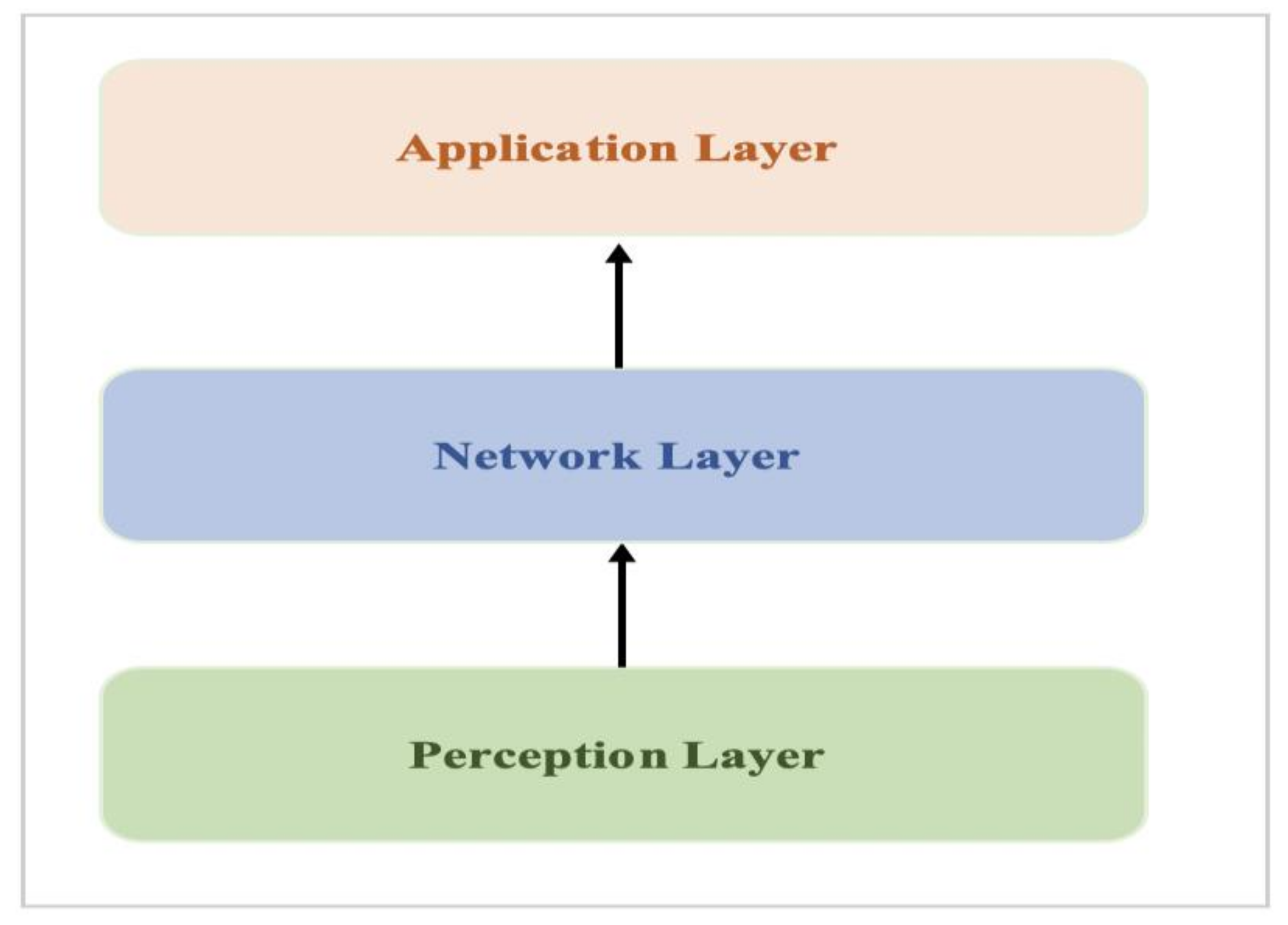
Electronics | Free Full-Text | Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions