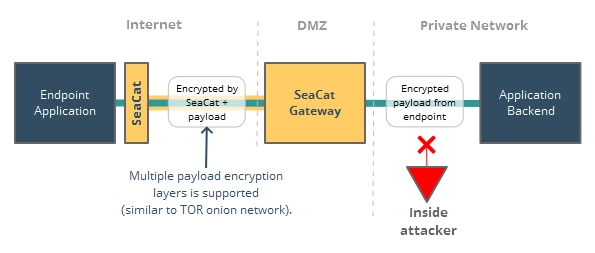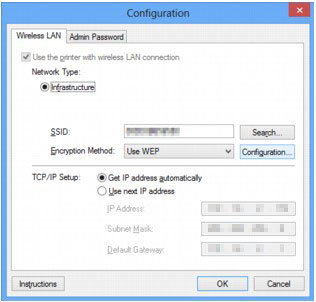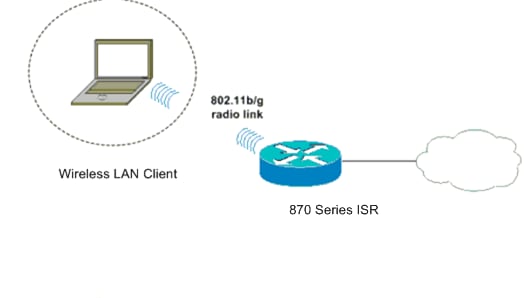
Wireless LAN Connectivity using an ISR with WEP Encryption and LEAP Authentication Configuration Example - Cisco

300Mbps In-Wall Wireless Router AP Access Point WiFi Router LAN Network Switch WiFi AP Router with WPS Encryption USB Socket Grey - Walmart.com

300Mbps In-Wall Wireless Router AP Access Point WiFi Router LAN Network Switch WiFi AP Router with WPS Encryption USB Socket White - Walmart.com

300Mbps In-Wall Wireless Router AP Access Point WiFi Router LAN Network Switch WiFi AP Router with WPS Encryption USB Socket Black - Walmart.com

WIRELESS LAN SECURITY ATTACKS AND CCM PROTOCOL WITH SOME BEST PRACTICES IN DEPLOYMENT OF SERVICES | Semantic Scholar


:max_bytes(150000):strip_icc()/comtrend-wireless-security-settings-5c47a3a646e0fb00019eb742.png)






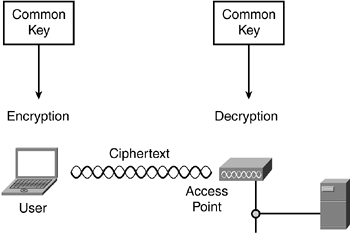
![802.11 Network Security Fundamentals [Cisco Secure Services Client] - Cisco Systems 802.11 Network Security Fundamentals [Cisco Secure Services Client] - Cisco Systems](https://www.cisco.com/en/US/i/200001-300000/270001-280000/270001-271000/270661.jpg)