Data Information Network Security Firewall Video Dedicated Physical Security Isolation And Switching System Air Gap - Buy Air Gap,Physical Security Isolation Computer Product on Alibaba.com

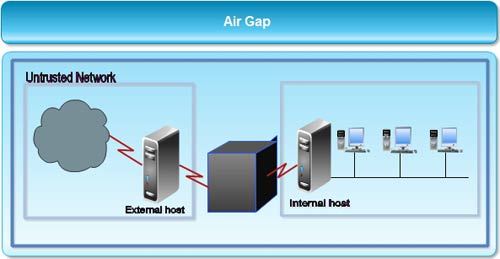
Sensors | Free Full-Text | A Survey on Air-Gap Attacks: Fundamentals, Transport Means, Attack Scenarios and Challenges

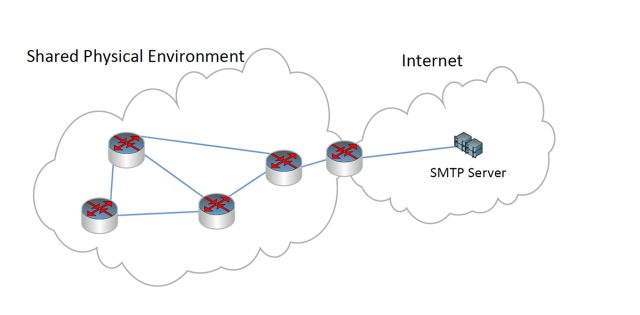
Sensors | Free Full-Text | A Survey on Air-Gap Attacks: Fundamentals, Transport Means, Attack Scenarios and Challenges

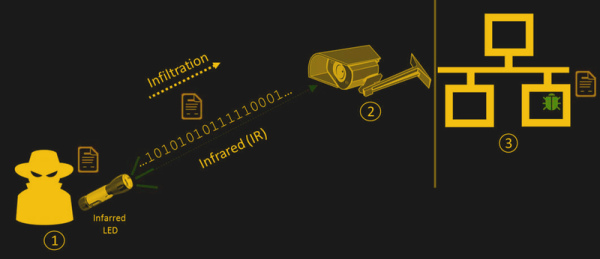
aIR-Jumper: Covert air-gap exfiltration/infiltration via security cameras & infrared (IR) - ScienceDirect

Data Information Network Security Firewall Video Dedicated Physical Security Isolation And Switching System Air Gap - Buy Air Gap,Physical Security Isolation Computer Product on Alibaba.com

Sensors | Free Full-Text | A Survey on Air-Gap Attacks: Fundamentals, Transport Means, Attack Scenarios and Challenges

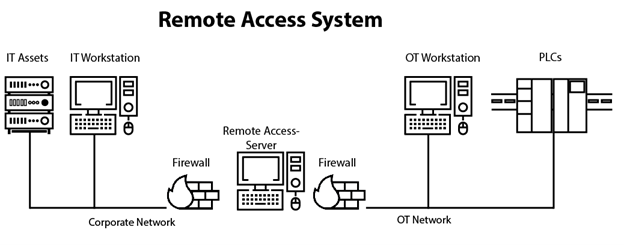
Design-based Fortifications | Cyber-security in Industrial Measurement and Control Systems | Textbook